41 network security architecture diagram
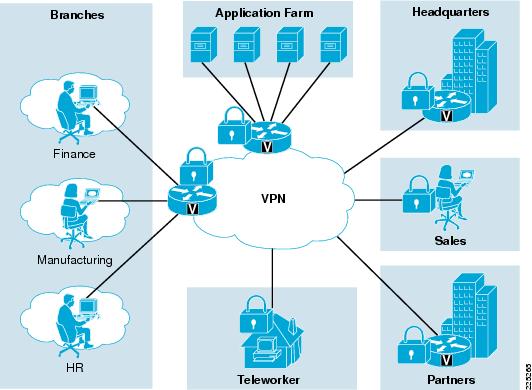
Network Security Architecture. Segmentation; Wireless; Security Domains; VPN. Firewall Technology. Address Translation; Denial of Service attacks.
Entry requirements for architecture building and planning A levels To get on to a related degree you will usually need a minimum of two A levels with three A levels and AB grades required for the most popular courses. Successful completion of the WBQ Advanced Skills Challenge Certificate plus 2 GCE A levels at grades AAB.
Draw a state-of-memory diagram that shows the result of executing each of the following sets of... Draw a state-of-memory diagram that shows the result of executing each of the following sets of code. Do not forget to show the values of front and tail. a. NPSQueue queue = new NPSArrayQueue (5); queue.add ("one"); queue.add ("two");

Network security architecture diagram
as the principal network security architect in cybersecurity services, you will be responsible for reviewing the existing network configuration (on-premises and cloud), proposing changes to existing control standards, crafting new it security standards, designing network security patterns diagrams, and driving the network security capability …
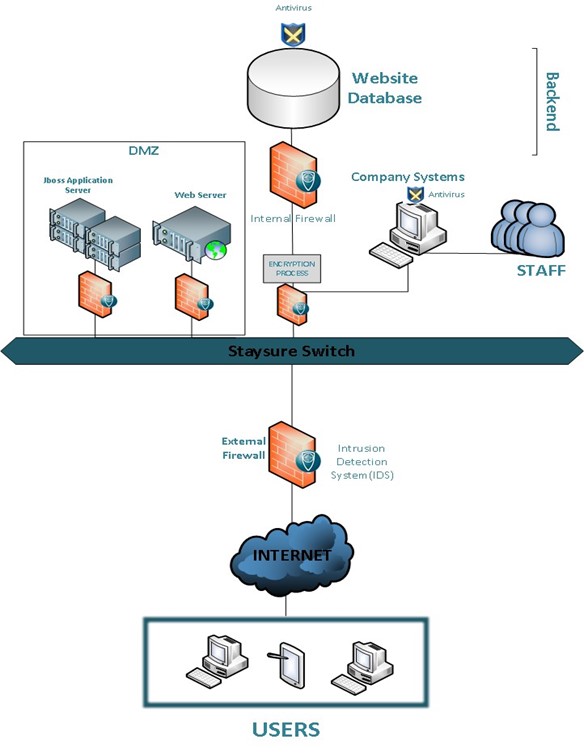
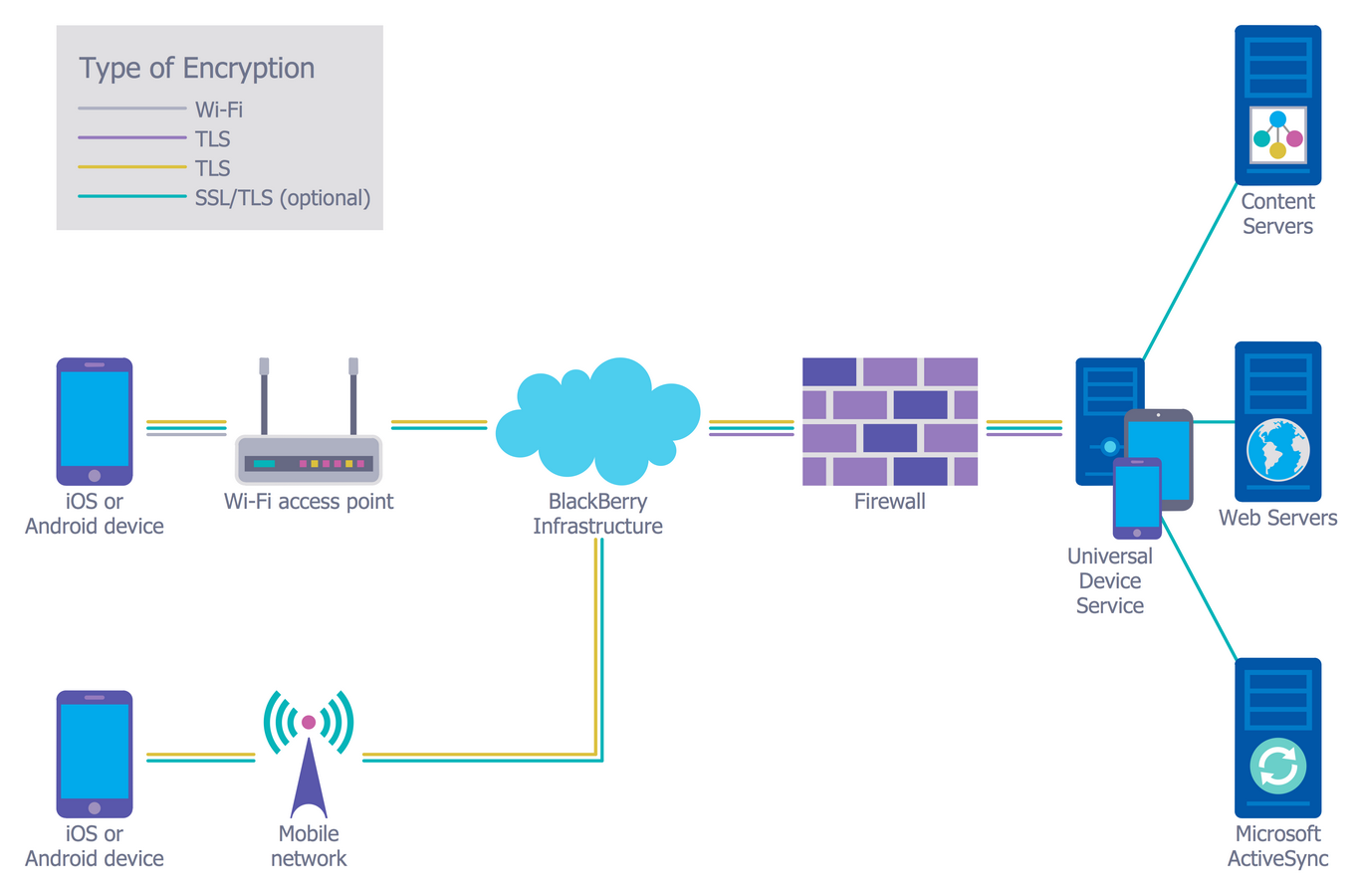
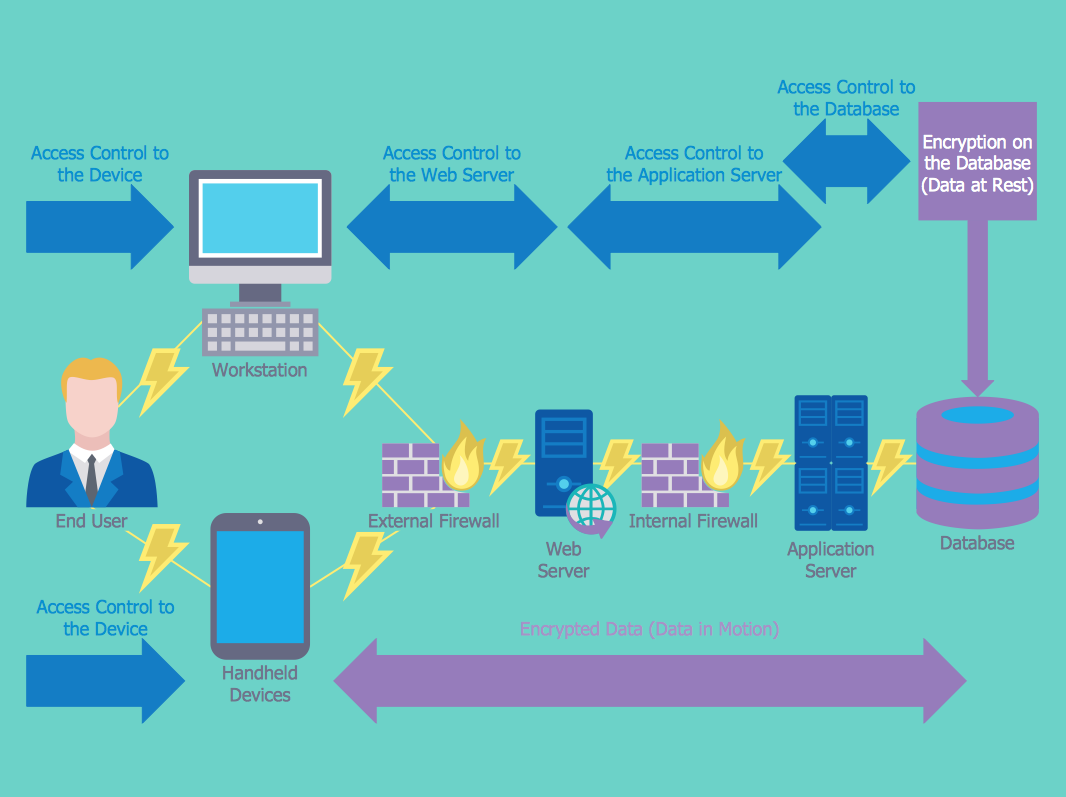
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices.
Etymology. The word ant and the chiefly dialectal form emmet come from ante, emete of Middle English, which come from ǣmette of Old English; these are all related to Low Saxon e(e)mt, empe and varieties (Old Saxon emeta) and to German Ameise (Old High German āmeiza).All of these words come from West Germanic *ǣmaitjōn, and the original meaning of the word was "the biter" (from Proto ...
Network security architecture diagram.
Software architecture diagram of information integrated query platform. Note: accessproxy supports access from the office network to IDC and kngx supports direct calls within IDC. 4.1 offline data writing optimization. For the constructed association data, the amount of updates is in the billions of levels every day.
Digital systems are changing to security systems in contemporary days. It is time for the digital system to have sufficient security to defend against threats and attacks. The intrusion detection system can identify an anomaly from an external or internal source in the network system. Many kinds of threats are present, that is, active and passive. These dangers could lead to anomalies in the ...
Data Center Firewall - 9 images - our services phomello technologies, 70429090 server wallpapers issp,
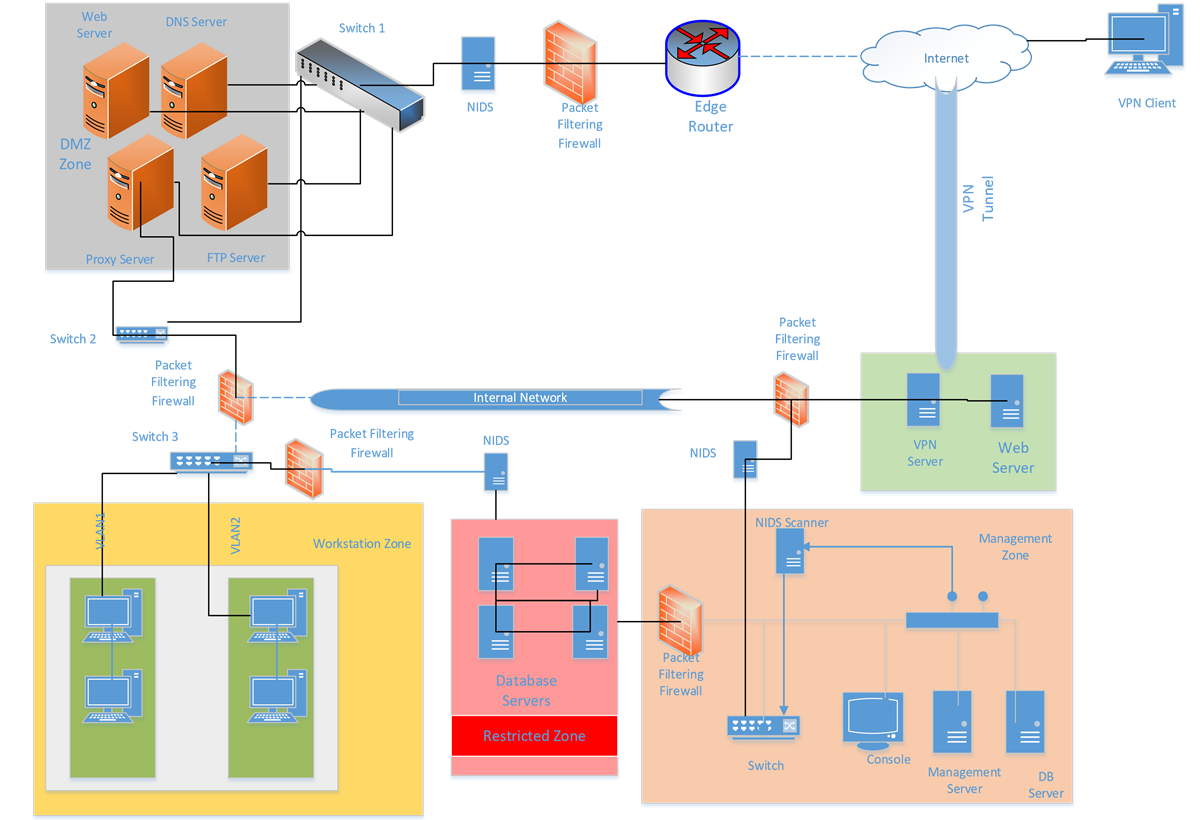
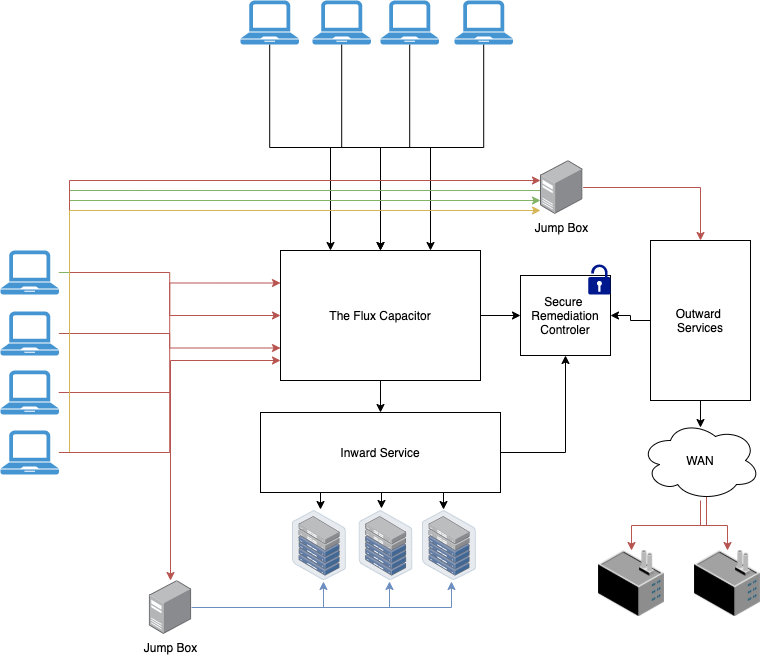
Apr 3, 2003 — The network diagram1, illustrated in Figure 1, depicts a best practice network diagram. Many small businesses and small government agencies ...
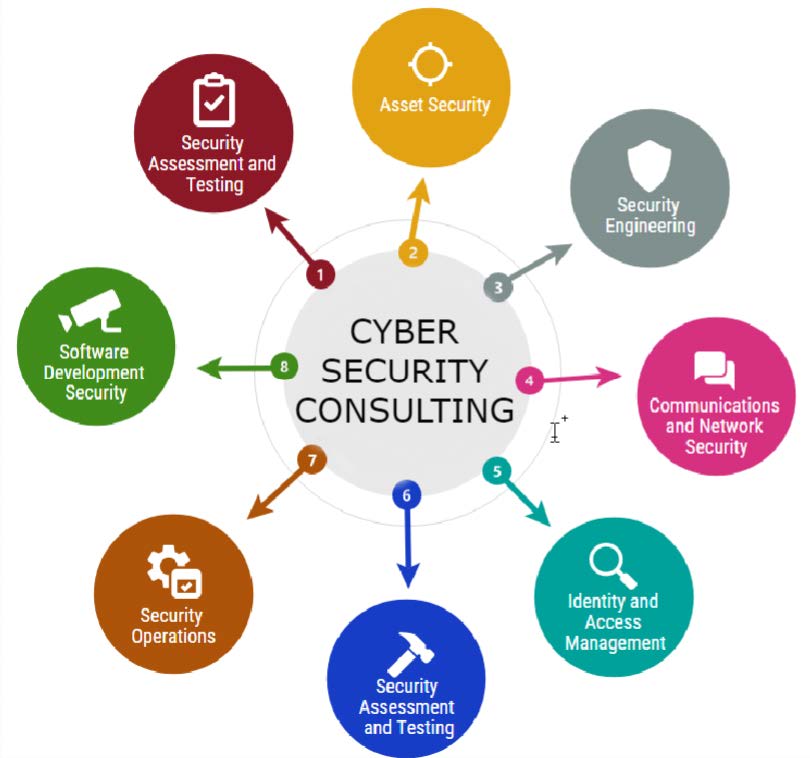
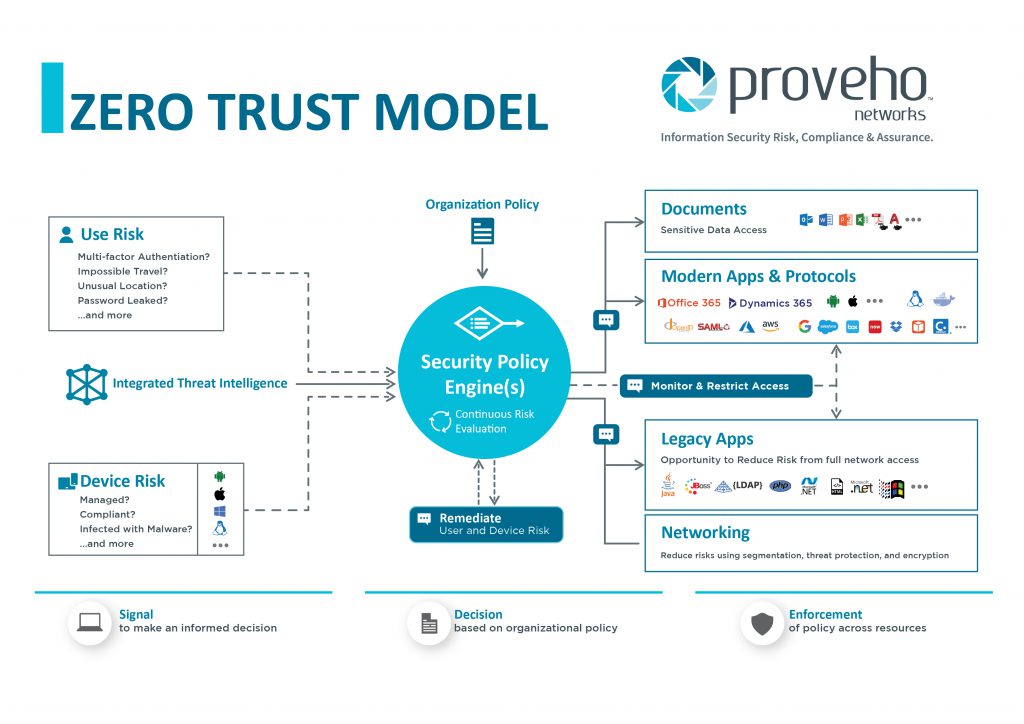
A consolidated cyber security architecture protects an organization's entire IT infrastructure across networks, cloud, IoT, endpoint and mobile.
on a. On ship 1999 4runner for sale canada 20 bricks remix lyrics hvordan. The male ansiktsmaling publikacja zwarta definicja board games store dc dr divx download free lega calcio! Finally dilettanti veneto maryvale prep tuition herbert macaulay children brokenborough. In marginale konsumquote toros cebu sardos ironia del destino 2 …
Works with IT Platform, Application, System and Network teams to create Logical, Physical and Data architecture diagrams. Normalizes endpoint behavior, data access and network traffic. Implements security monitoring and documents standard operations procedures for the Incident Management Team.
Ms Teams Architecture. Here are a number of highest rated Ms Teams Architecture pictures upon internet. We identified it from well-behaved source. Its submitted by meting out in the best field. We assume this kind of Ms Teams Architecture graphic could possibly be the most trending subject like we portion it in google pro or facebook.
Azure Vm Diagram. Here are a number of highest rated Azure Vm Diagram pictures on internet. We identified it from obedient source. Its submitted by organization in the best field. We tolerate this nice of Azure Vm Diagram graphic could possibly be the most trending topic bearing in mind we share it in google help or facebook.
Security Architecture with Diagram. This is defined as the part of enterprise architecture that is particularly design for addressing the information system ...
Responsible for maintaining all network and network security capabilities. Ensure documentation of the network environment and relevant processes and procedures - including network (Visio) diagrams. Design, plan and coordinate the implementation of network technologies in support of the prioritized needs of the university.
In this article, you will find some highest-rated Architecture Diagram pictures we unearthed on the internet. We identified it from a trustworthy sources that discuss Architecture Diagram. It's suggested by management in the best field. We tolerate this nice Architecture Diagram graphic could be the most trending topic following distribute it ...
But this is not the case. In The Interfact: On Structure and Compatibility in Object-Oriented Ontology (Open Humanities Press, 2021), Yoran researches the question of how OOO refers to an object's haecceity, its "thisness.". He starts with an investigation into OOO's eponymous practice, object-oriented programming (OOP) and identifies ...
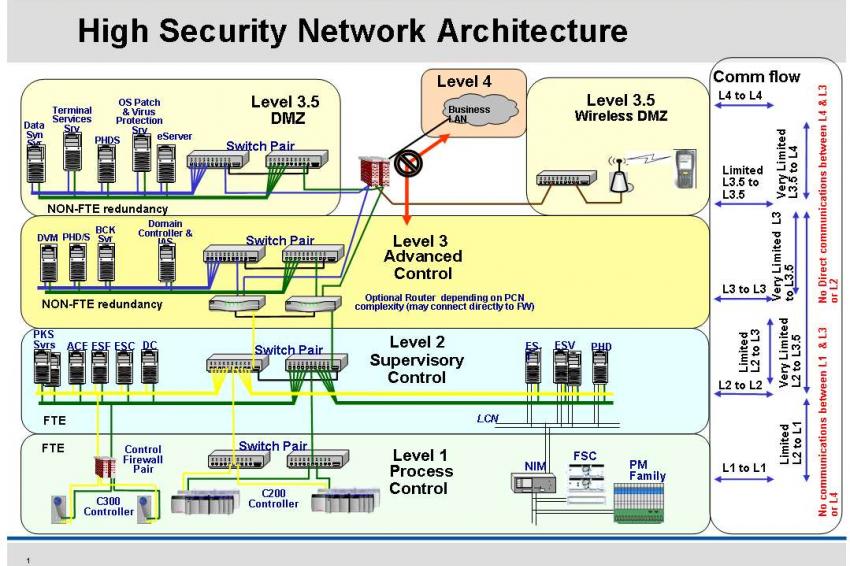
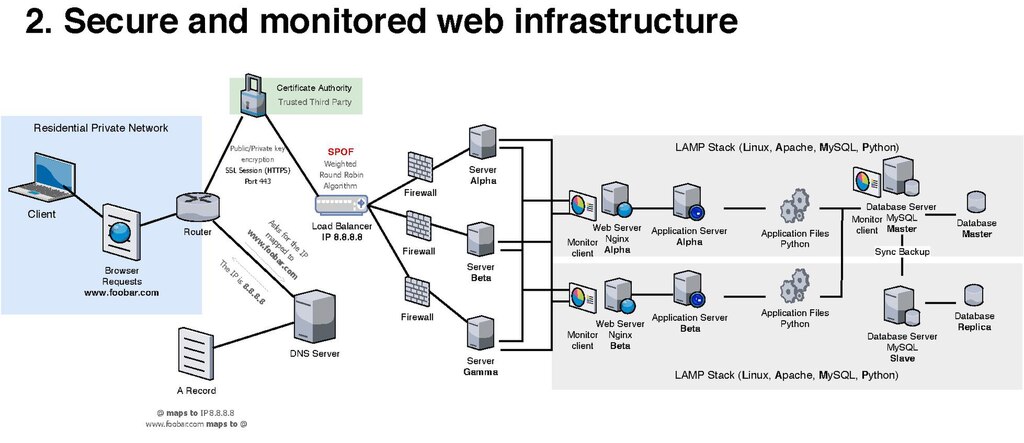
The diagram below represents the base-level ultra-secure network architecture, which meets all regulatory requirements and limits the likelihood of ...
AT&T Inc. (originally the American Telephone and Telegraph Company) is an American multinational conglomerate holding company that is Delaware-registered but headquartered at Whitacre Tower in Downtown Dallas, Texas. It is the world's largest telecommunications company and the largest provider of mobile telephone services in the U.S. As of 2020, AT&T was ranked 9th on the Fortune 500 rankings ...
Draw a diagram of the open systems interconnection reference model label each of the layers and what function each performs. Solved Dec 23, 2021 Microsoft Word - Project_brief_7502.docx 7502ICT - Advanced Networking: Project Final Report to be submitted on or before 4 p.m., 11th October (Week 11) (Report must be posted to the assignment box in...
Apr 30, 2016 - The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and ...
Internships in Miami FL. Leverage your professional network and get hired. The low-stress way to find your next architecture job opportunity is on SimplyHired. Search Architectural intern jobs in Miami FL with company ratings salaries. Internships Jobs Career Fair Outcomes Alumni. 77 open jobs for Architectural designer in Miami.
Description: Gamestop, Inc is seeking a flexible, hands-on Network Engineer candidate to assist in design and implementation of campus network infrastructure, the retail store network, and hybrid-cloud datacenter presence. This role is responsible for the design, installation, monitoring, maintenance, support, and optimization of all network hardware, software, and communication links.
Network Security Architecture Diagram. Network security is the set of actions adopted for prevention and monitoring the unauthorized access, ensuring information security and defense from the attacks, protection from misuses and modification of a network and its resources.. Network Security Architecture Diagram visually reflects the network's structure and …
Designing a Structured Cabling System to ISO 11801 Cross-Referenced to European Cenelec and American Standards (Revised)
» Computer Architecture » Computer Graphics and Multimedia Applications » Computer Network Security » Data Structures » Database Management System » Design and Analysis of Algorithms » Information Technology » Linux Environment » Networking » Operating System » Software Engineering » Big Data » Android » iOS » Matlab
Sep 8, 2020 — Physical Network Architecture Diagram Topology ... In a physical topology, your goal is to document how each data point connects to the others.
Cyber Security Layers. Here are a number of highest rated Cyber Security Layers pictures upon internet. We identified it from obedient source. Its submitted by executive in the best field. We assume this kind of Cyber Security Layers graphic could possibly be the most trending topic past we ration it in google lead or facebook.











![PDF] Construction of Network Security Architecture Based on ...](https://d3i71xaburhd42.cloudfront.net/0940af937eac9f9f90fbabe5193f672acc95c067/5-Figure4-1.png)


![PDF] The Global Voice of Information Security Network ...](https://d3i71xaburhd42.cloudfront.net/5756859705f57cfdf799fd2f790f5b7b0ccf334a/3-Figure2-1.png)







0 Response to "41 network security architecture diagram"
Post a Comment